What Are Jscripts Viruses?
Jscripts viruses, otherwise called JavaScript-based viruses, are a kind of malware developed in JavaScript to leverage vulnerability in web applications, browsers, or operating systems.
Unlike real viruses, which might need user interaction to be activated, Jscripts viruses self-execute by simply visiting a booby-trapped website or just opening an email with malicious content.
These viruses are often cloaked in innocuous-looking scripts and sit inside huge libraries of codes that a developer tends to reach out to time. Once activated, they can do everything from stealing sensitive data to redirecting users to phishing sites or taking control of their devices.
The Silent Infiltration: How Jscripts Viruses Spread?
One of the most dangerous features of Jscripts viruses is that they propagate extremely quickly and silently. Here’s how they normally get into a developer’s codebase:
Third-Party Libraries
Developers make use of third-party libraries and plug-ins to speed up development. But these libraries are infected, they will act as a gateway for Jscripts viruses to get into your code. Usually, a developer trusts these libraries; a malicious script can easily go through.
Phishing and Social Engineering
Cybercriminals often use phishing techniques to trick developers into downloading and executing malicious scripts. An innocuous email with an attachment or the link to some “helpful tool” can be a vector of a Jscripts virus.
Code Repositories
Public code repositories are extremely helpful but, at the same time, can be a source of risk. Malicious actors could upload infected code that developers may use in their apps.
Cross-Site Scripting (XSS)
XSS injects bad scripts into web applications. If your application is vulnerable, a hacker could use it to propagate Jscripts viruses to other users.
Real-World Consequences: What Can Go Wrong?
If a JScripts virus gets into your code, that can be disastrous for you & your users, and your clients. Here’s how this might go wrong in the worst case:
Data Breaches:
Jscript viruses may further steal sensitive information, such as usernames, passwords, and financial data. The user’s trust is compromised & this can result in several legal cases of negligence in protecting the user’s data.
Website Defacement:
At times, these Jscripts viruses can be used by attackers to modify content on your website, which can damage your reputation. This can lead to other visitors being redirected to malicious sites or displaying inappropriate content to visitors.
Financial Loss:
On e-commerce websites, a Jscripts virus can self-execute money transactions for unauthorized transactions resulting in huge losses. Additionally, disinfecting an infection cost and returning the site to operation can be expensive.
Damage to Prestige:
Furthermore, if your project or application is reported to distribute malware, it will badly hurt your reputation as a developer. Confidence and trust are at stake when clients or users use secure products delivered by clients.
Ways to detect Jscripts viruses in your code
The thing is, detecting Jscripts viruses may be tough because they are written to resemble regular code. Several techniques and tools can identify a potential threat:
Code Reviews:
Regular code reviews should be practiced to detect suspicious scripts. Several developers should be involved without letting any potentially harmful code pass through and get deployed.
Static Code Analysis Tools:
Run code with the help of static code analysis tools, which can automatically scan your codebase for potential vulnerabilities and suspicious patterns. Tools like ESLint, SonarQube, JSHint, and others will help maintain code quality and safety.
Network Traffic Analysis
Activity on the network can be nonlinear, thereby providing a suspicion that something is wrong, similar to a Jscripts virus. If your application is sending out data to strange or suspicious IP addresses, then there could be something going on that may need to be looked into.
Dependency Scanning:
Testing your dependencies for vulnerabilities regularly. Tools like npm audit, Snyk, and OWASP Dependency-Check will allow you to detect and reduce risks coming from third-party libraries.
Behavioral Analysis
Sometimes static analysis isn’t enough. Behavioral analysis involves executing the scripts in a controlled environment and observing the behavior of the process. You can notice probable malicious activities aren’t visible while looking at the code.
The Encounter
One of our clients contacted us regarding bug bounties for an open-source project. After a brief, engaging conversation about various tech domains, the client asked if we could check out their code to identify any hidden issues.
Then we are provided a link to a ‘big bucket URL’—an unusual name & we initially thought maybe it was one of those trendy code repositories. Intrigued but cautious, we requested to see the site first.
When they claimed that URLs aren’t deployed yet, we all assumed “Okay, maybe they are just in the early stages.” Curiosity piqued, and we had a chance to clone the repository.
As we traversed through the code, something caught our eye—a config file with an extraordinary amount of whitespace followed by some peculiar script. Intrigued and weirded out, we all delved deeper and discovered a Trojan virus!
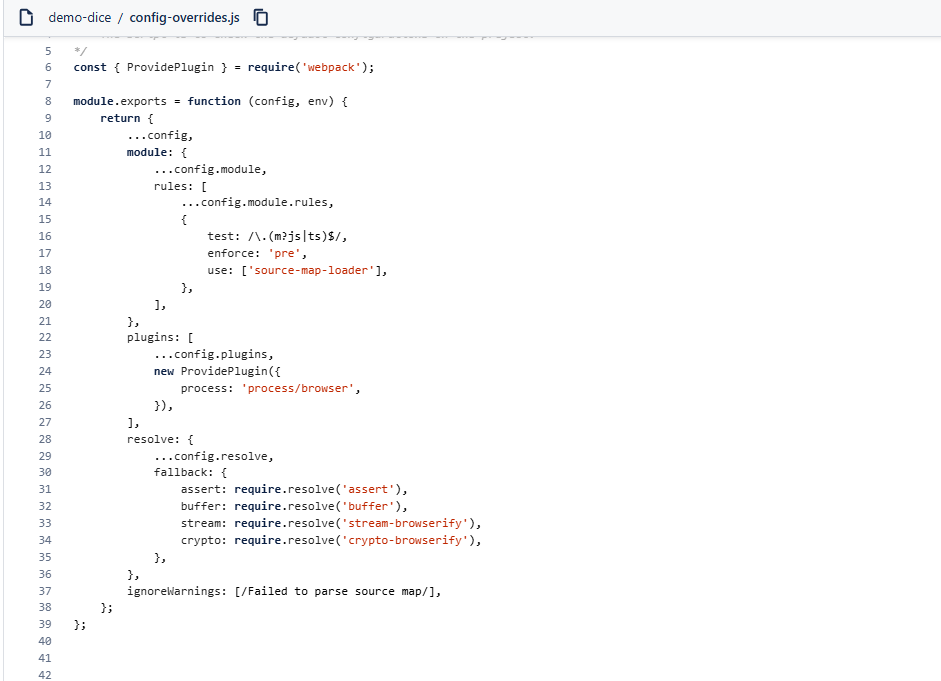



We hastily opened the `package.json` file to analyze the scripts—good practice, right? It showed multiple strange scripts, and then we realized these were orchestrated to execute the Trojan silently once we ran the typical setup commands. It was an elaborate trap!
What Does a Trojan Look Like?
Here’s a chunk of how the `package.json` appeared:


With the `npm start` command, it ominously directed to a `config-overrides.js` file, which was where the Trojan was lurking—14000 lines down! we couldn’t believe it. How easily could someone fall victim to this, if they missed that gem of a snippet hidden away? It’s astounding how quickly malicious scripts can infiltrate our systems under the guise of legitimate code
Keeping our cool, we launched a virtual machine to isolate potential damage. It was crucial to observe what changes it tried to instigate. Upon executing, we witnessed some sneaky file creations appear in our user directories—not a good sign!
In brief, this script tries to install an application with backdoor access, effectively allowing hackers to gather personal information from our system. Talk about shivers down your spine!
Best Practices to Prevent Jscripts Viruses
“Prevention is better than cure” goes the cliché, especially with Jscript viruses. So, here are some best practices to keep your code safe:
Use Trusted Sources
Third-party libraries and plugins should only be used from trusted sources. Be sure the library is recursively one is going to use is actively maintained and secure by checking reviews, maintainers, and the frequency of updates.
Implement Content Security Policy:
A Content Security Policy helps avoid XSS attacks by indicating sources of content that would be considered legitimate to load in a browser. It minimizes the risk of Jscript viruses by allowing less access when scripts need to be executed.
Keep Dependencies Updated:
A current dependencies list would mean automatically receiving the security patches and updates on the dependencies you rely on since obsolete libraries are a popular path attackers use to gain entry.
Train Your Team:
Awareness of the risks of Jscripts viruses should be imparted to all developers, who must also be trained in secure coding practices. Security training in this regard could help reduce the risk of human error.
Use Version Control Wisely:
Using version control systems like Git can change your codebase. If a Jscripts virus gets into the system, with version control, identifying its entrance time and place will be much easier, and thus it will be removed.
Back-Up:
When your codebase goes bad, nothing like a regular backup is useful. Backups must be safely kept and restorable as soon as possible if required.
Conclusion: Be Safe, Stay Vigilant
This is a real threat posed by Jscripts viruses, and it is upon you as a developer to ensure that your code does not contain malicious scripts. Remaining vigilant, following best practices, and using the right tools will help to protect projects and users against such hidden dangers.
Remember that the key to preventing Jscripts viruses lies in awareness and prevention. Every once in a while, review your code. Keep an ear to the ground for evolving security threats, and never take shortcuts in security. Your professional reputation as a developer and the safety of your users depends on that.Does it sound promising? Book a consultation call with us to learn more about our service offerings.